Wireless Application Protocol (WAP) is a technical standard
for accessing information over a mobile wireless network
. A WAP browser is a web browser
for mobile devices
such as mobile phones
that uses the protocol.
The WAP standard described a protocol suite allowing the interoperability of WAP equipment, and software with different network technologies, such as
GSM and IS-95 (also known as CDMA).
| Wireless Application Environment (WAE) | WAP protocol suite |
| Wireless Session Protocol (WSP) |
| Wireless Transaction Protocol (WTP) |
| Wireless Transport Layer Security (WTLS) |
| Wireless Datagram Protocol (WDP) |
| *** Any Wireless Data Network *** |
The bottom-most protocol in the suite, the Wireless Datagram Protocol (WDP), functions as an adaptation layer that makes every data network look a bit like UDP to the upper layers by providing unreliable transport of data with two 16-bit port numbers (origin and destination). All the upper layers view WDP as one and the same protocol, which has several "technical realizations" on top of other "data bearers" such as SMS, USSD, etc. On native IP bearers such as GPRS, UMTSpacket-radio service, or PPP on top of a circuit-switched data connection, WDP is in fact exactly UDP.
WTLS, an optional layer, provides a public-key cryptography-based security mechanism similar to
TLS.
WTP provides transaction support (reliable request/response) adapted to the wireless world. WTP supports more effectively than TCP the problem of packet loss, which occurs commonly in 2G wireless technologies in most radio conditions, but is misinterpreted by TCP as network congestion.
Finally, one can think of WSP initially as a compressed version of HTTP.
This protocol suite allows a terminal to transmit requests that have an HTTP or
HTTPS equivalent to a WAP gateway; the gateway translates requests into plain HTTP.
he WAP Forum
dates to 1989. It aimed primarily to bring together the various wireless technologies in a standardised protocol.[1] The first company to launch a WAP site was Dutch mobile phone
operator Telfort BV
in October 1999. The site was developed as a side project by Christopher Bee and Euan McLeod and launched with the debut of the Nokia 7110
.
In 2002 the WAP Forum, founded by Ericsson, Motorola, Nokia and Unwired Planet (later known as Openwave), was consolidated (along with many other forums of the industry) into Open Mobile Alliance (OMA]).
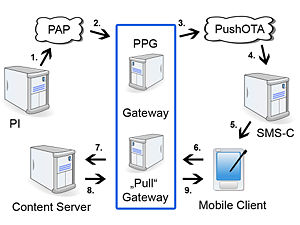
WAP Push
WAP Push was incorporated into the specification to allow the WAP content to be pushed to the mobile handset with minimum user intervention. A WAP Push is basically a specially encoded message which includes a link to a WAP address.
WAP Push was specified on top of Wireless Datagram Protocol (WDP); as such, it can be delivered over any WDP-supported bearer, such as GPRS or SMS. Most GSM networks have a wide range of modified processors, but GPRS activation from the network is not generally supported, so WAP Push messages have to be delivered on top of the SMS bearer.
On receiving a WAP Push, a WAP 1.2 (or later) -enabled handset will automatically give the user the option to access the WAP content. This is also known as WAP Push SI (Service Indication). A variant, known as WAP Push SL (Service Loading), directly opens the browser to display the WAP content, without user interaction. Since this behaviour raises security concerns, some handsets handle WAP Push SL messages in the same way as SI, by providing user interaction.
The network entity that processes WAP Pushes and delivers them over an IP or SMS Bearer is known as a Push Proxy Gateway (PPG).
WAP 2.0[edit]
A re-engineered 2.0 version was released in 2002. It uses a cut-down version of XHTML with end-to-end
HTTP, dropping the gateway and custom protocol suite used to communicate with it. A WAP gateway can be used in conjunction with WAP 2.0; however, in this scenario, it is used as a standard proxy server. The WAP gateway's role would then shift from one of translation to adding additional information to each request. This would be configured by the operator and could include telephone numbers, location, billing information, and handset information.
Mobile devices process XHTML Mobile Profile (XHTML MP), the markup language defined in WAP 2.0. It is a subset of
XHTML and a superset of XHTML Basic. A version of cascading style sheets (
CSS) called WAP CSS is supported by XHTML MP.